|
|
Masters in Computer Science Alumni
Current Students (2012)
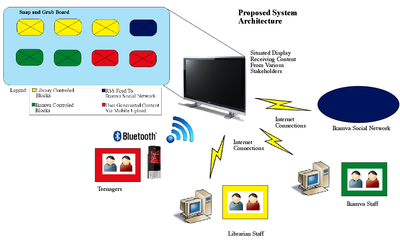
Situated Displays as a Facilitator to a Media Sharing
Culture
Media sharing amongst teenagers is a well-observed process all
across the world, our research continues this path, and in
particular, our aim is to analyze media sharing and usage of
African youth in townships. Specifically the purpose of this
research project is to analyze how teenagers make use of public
situated displays that store user generated content. From this
research we will determine some guidelines to which mobile phone
application developers could use to better cater for the
low-income teenage market and also develop technology to
facilitate media sharing activities.
|
|
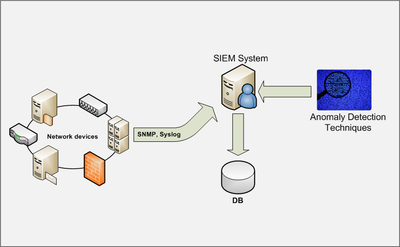
Evaluation of Anomaly Detection Techniques to Enhance SIEM Systems
| By |
Stefan Asanger |
|
Website |
None |
My research seeks to answer the question of whether anomaly
detection techniques can be used to enhance the capabilities of
Security Information and Event Management (SIEM) systems. Anomaly
detection is a promising approach in the field of network
security. My research will evaluate which techniques perform
best/worst in terms of performance and effectiveness and will give
recommendations in this regard. Testing will be carried out at a
financial services provider where the SIEM system “Tivoli Security
Operations Manager” is in use. This company will provide test data
and is willing to integrate anomaly detection into the SIEM system
to perform a field trial.
|
|
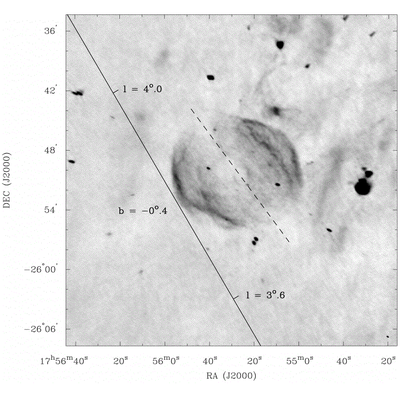
GPU-based Acceleration of Radio
Interferometry Image Synthesis
This project aims to expedite the processing of Astronomical Radio
Interferometry UV data to produce multi-frequency data and images
useful to Astronomy researchers with the use of GPU cards. A GPGPU
implementation of Direct Fourier Transform method of Image
Synthesis will be developed, optimized, and tested against
standard Fast Fourier Transform and multi-core implementations.
Auto-tuning will be implemented if deemed necessary. This project
will probably be extended to include other GPU related enquiries,
that of 3D Direct Fourier Transforms, Deconvolution methods or
both.
|
|
Accelerated Crowd Modelling
The application of High-Level Constraints to Fuzzy Crowds has been
shown to be feasible for small crowds but impractical for crowds
with more than a hundred agents. However the special effects
industry often requires crowds with thousands of agents. Using
CUDA and multi-threading techniques we have scaled the simulation
vertically achieving speedups of over 30x on a single node. Using
MPI we hope to scale the simulation horizontal achieving linear
speedup with the number of nodes in the cluster. Image: See
attachment.
|
|
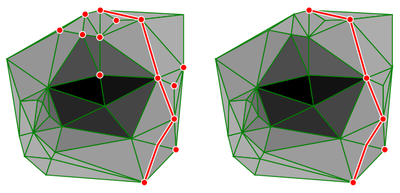
Path Planning in Weighted Regions
In Artificial Intelligence (AI) finding the shortest path in a
graph is a classic problem that has many efficient solutions. To
speed up path finding in known environments, there are many
techniques which preprocess the graph. However, none of these
techniques have been applied to the Weighted Region Problem. The
weighted region problem is finding the shortest path from a source
to a destination in a planar subdivision in which each region has
a weighting. The aim of my research is to apply different
preprocessing techniques to the weighted region problem and
evaluate them.
|
|
Wireless communication model for a better quality of Service in
Rural areas
Due to the small number of people in rural areas telephone
companies do not find it cost effective to install telephone
infrastructure there. Mesh potato (MP) is a solution. A MP is a
plain old telephone(POT) connected to a wireless node/access point
and allows individuals to make phone calls much like a land
line. It is still in its infancy stages and has room for
improvement. We seek to improve on it at the routing protocol. The
protocol used is called better approach to mobile as-hoc
networking or just B.A.T.M.A.N. In this project we are
investigating the development of a new quality of service (QOS)
routing scheme that will enable the MP to generate a better QoS in
this network.
|

|
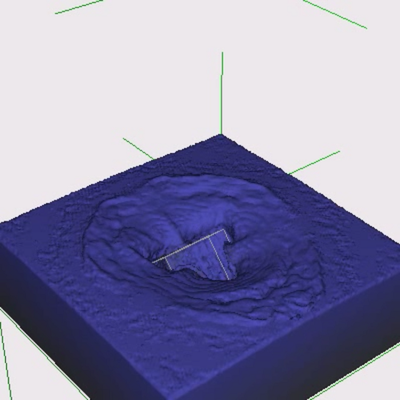
Lattice Boltzmann Liquid Simulation with Moving Objects on
Graphics Hardware
The Lattice Boltzmann Method is used to simulated fluids with
moving obstacles. These simulations are implemented on the GPU
using CUDA to vastly reduce the required simulation time. The
simulation includes the liquid's free-surface, tracked using the
Volume of Fluid method. The Lattice Boltzmann Method is a Eulerian
(grid-based) method that is linear with respect to time, and
requires no global communication, which makes it particularly
well-suited to parallel architectures. Moving obstacles are
simulated using Bullet Physics which interfaces with the fluid
simulation when calculating fluid-obstacle momentum transference.
|
|
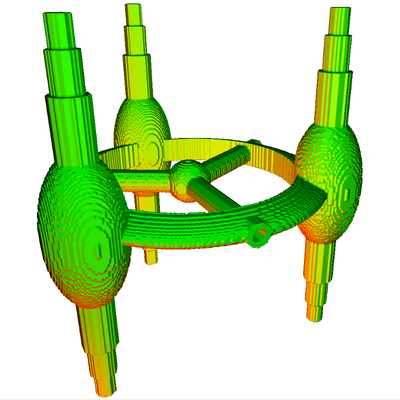
Procedural Generation of Spacecraft
Using Shape Grammars
The aim of this project is to develop a method of procedurally
generating spacecraft that would be suitable for use in video
games and film special effects. Our work is based on existing
shape grammar methods, but we will extend these with features such
as voxel-space interpretation and symmetry. It is likely that
these extensions will be applicable to other areas of procedural
generation, such as the shape grammars used to create
buildings. We have also planned a thorough set of tests for
evaluating our work, and ensuring it meets the desired requirements.
|
|
Detection of drivable regions for
autonomous robots applied to South Africa underground
mining
The process of extracting ore or minerals from the ground remains
one of fundamental interest as it generates a lot of resources.
However, miners often undergo a lot of risks, and a lot of
hazardous events such as blasting often arise. The increasing
mortality rate of miners remain an issue of great concern to the
miners and the environment at large. Autonomous robots would play
a vital role in this area. Hence, the need to provide supportive
navigational strategy to aid the preventive safety operations
performed by autonomous robots
|

|
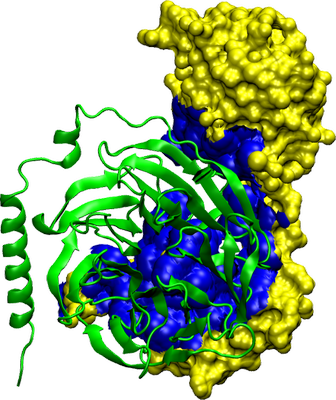
Computational tools for
protein-protein interface analysis
We calculate triangulated surfaces of binding interfaces in
non-redundant protein-protein complexes from the PDB with our
software, Piech. Our large data set and fine-grained
surface calculations enables a more statistically significant
survey than was previously possible. We find tha homo- and
heterodimeric complexes have similar, very broad distributions of
interface area, with an "average" interface size of around
1,200Å. We identify distinctive interface residue propensity
patterns for different classes of proteins, particularly at the
core of the interface. Hydrophobic residues are strongly favoured
at the core regions of both hetero-and homomers, but not as
favoured in immune protein complexes. This work evaluates the
largest number of protein-protein interfaces to date.
|
|
Resource Sharing in Mobile
Peer-to-Peer
| By |
Martha Kamkuemah |
|
Website |
None |
This research deploys a P2P application in a mobile ad hoc
environment. The P2P network will consist of limited-resource
mobile phone nodes that form a temporary network anywhere without
much infrastructure investment which is typical mobile ad hoc
networks (MANETs). The P2P network will use the Freenet
steepest-ascent hill-climbing search mechanism to search for and
share resources. This search mechanism will be compared to other
search mechanisms used in popular P2P networks such as Gnutella.
Through system evaluation the searching and routing metrics as
well as the upload and download times of nodes in the network will
be compared to similar properties in a Gnutella network.
|
|
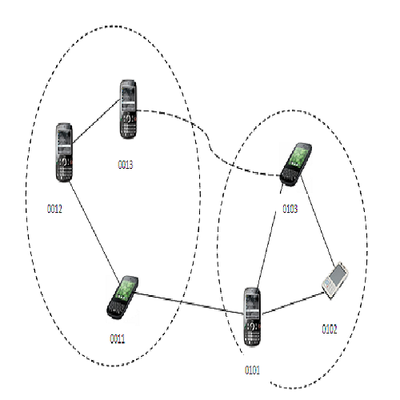
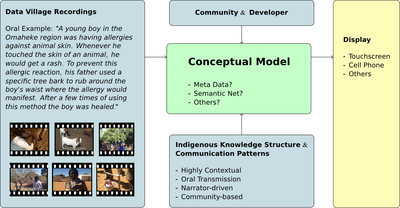
Gereon Kapuire
In this project we will endeavor to develop an indigenous
knowledge management system for indigenous knowledge for a
selected local community, as a proof of concept. As current
systems do not support the social-cultural and communication
structures of communities, my study focus is to discover and
collect ICT design ideas and structures from the community for the
purpose of storage and retrieval of indigenous knowledge and map
the life style into an appropriate ICT indigenous knowledge
retrieval architecture. The retrieval techniques and processes
will be assembled from the identified rural community as a result
of mapping existing knowledge transfer and communication patterns
onto the system. As part of a long-term collaborative research
project, the indigenous knowledge retrieval architecture will then
become part of the indigenous knowledge management system to be
developed.
|
|
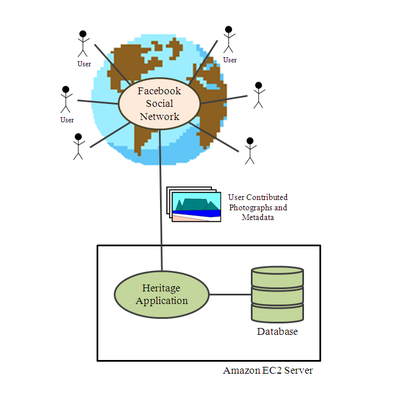
Building Heritage Collections Using
Games on Social Software
The collection of heritage data is a time-consuming and expensive
process and is often dependent on project funding. However this is
not sustainable. Therefore it is necessary to find cost-efficient
and time-efficient ways of preserving heritage data. A solution
may be to exploit social networks and the way in which people
interact. An application on a social network may provide a means
to avoid the cost, decrease time and increase scale of operation
of heritage preservation by motivating users to supply and process
the data. This project aims to use a Facebook application for the
purpose of gathering heritage data and useful metadata.
|
|
Realistic Procedural Forest
Generation and Rendering
Forests are an important part of many scenes in computer games
and simulations. Due to the high complexity involved, various
tricks have to be employed in order to facilitate their use in
games and simulations. These tricks often have a negative
impact on a game's visual appearance. This project deals with
techniques to mitigate these effects by using procedural
generation and level-of-detail tools. Specifically we will be
investigating L-Systems and various tree placement strategies
to generate realistic forests within reasonable performance
limits.
|

|
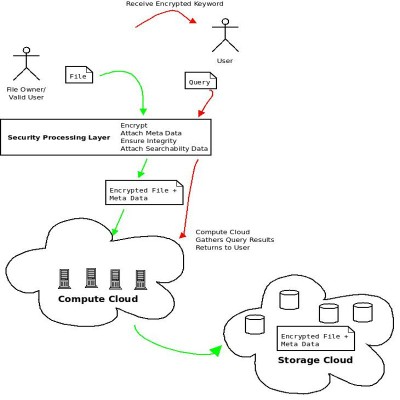
A Generic interface for Secure
Searchable Storage on a Public Cloud
The aim of this research will be to develop a technique that
will allow users to securely store private data on a public
cloud such as Amazons S3 and analyse the impact such a system
will have on terms of a performance overhead. The system must
allow for sharing of data, assign certain rights to other
users and revoke them, and it must be able to validate the
integrity of the file. Along with being able to store data the
concept of Searchable Encryption and its application in this
context will also be explored.
|
|
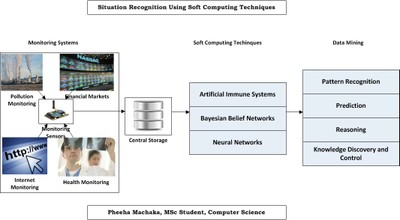
Situation Recognition Using Soft
Computing Techniques
In many domains such as infrastructure management, business
process monitoring, crisis management and other monitoring
activities, systems are characterised by large numbers of sensors
collecting data from a variety of information sources. The
information is collected in real-time and thus there is an
interest for live performance analysis and reporting.
This calls for data mining methods for recognising, predicting,
reasoning and controlling performance of systems. In recent years,
soft computing methods and algorithms and methods have been
applied to data mining, to identify patterns and new insight into
data.
Three soft computing techniques were chosen, namely, Artificial
Immune Systems, Bayesian Belief Networks and Neural Networks.
In this project, soft computing techniques are applied to
different datasets including the Wi-Fi network monitoring data,
Kenya drought data and the pollution monitoring data. In this way,
we can determine which of the techniques and algorithms work best
under which circumstances.
|
|
Interference Mitigation in Wireless
Sensor Networks
The objective of this project is todevelop interference mitigating
techniques that will allow Wireless sensornetworks to communicate
effectively and reliably in collocating environmentswhere other
sources of wireless devices exist and which are capable
ofdisrupting communication in a sensor network. The first step in
mitigatinginterference is the ability to detect it. Thus the first
phase of this project isdedicated to selecting tools and
parameters that can effectively detect thepresence of
interference. These are then used in developing algorithms
whichcan cognitively adjust the operating behavior of the
sensornodes (in order to improve communication performance) based
on the interferenceexperienced in the working environment. The
last phase of this project involvesrunning experiments to test the
effectiveness of the mechanisms utilized to mitigate interference
on sensor networks.
|

|
Mobile versus Desktop: Comparing
Platforms for Information Dissemination and Search amongst
Youth in Low-income Communities
Research in digital literacies and mobile technology use in
low-income communities of South Africa has revealed the ubiquity
of the mobile Internet in such settings. Exceptional adoption
rates demonstrate the value that such technology offers by
providing affordable communication for many who were previously
unconnected. This project will extend our understanding of this
behaviour by directly comparing two systems for information search
deployed on different platforms: the conventional web and the
mobile medium. Both controlled experiments and a longitudinal
study will be employed in order to measure usability as defined by
ISO 9241-11 and to gather data about actual use.
|

|
Providing efficient and intelligent
communication between isolated networks
The main aim of this project is to improve the quality of the
communication between isolated networks using a data mule. The
data mule is a combination of a vehicle and an electronic device,
with the purpose of picking up data from one network when in close
range, buffering it and dropping it off in another network
wirelessly.
In order to achieve the main aim, we will develop a
new algorithm. An integral part of the development includes the
use of data mules that prioritizes on efficiency (packet loss and
latency) and intelligence (adaptability of communication in
changing situations) of data transmission between isolated
networks.
|

|
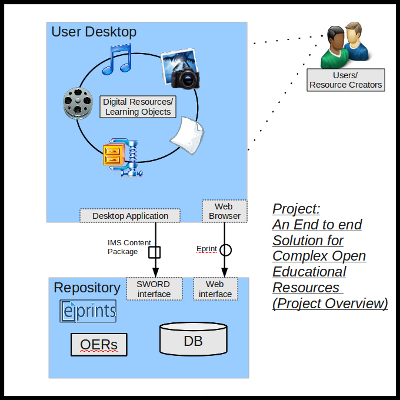
An End to End solution for Complex
Open Educational Resources
Open access and open resources have gained much attention from the
world in the last few years. The interest in sharing information
freely by the use of the World Wide Web has grown rapidly in many
different fields. Now, information is available in many different
data forms not only documents because of an evolution in
technology. This research focuses on Open Educational Resources
(OERs) and how educators supply their resources to the public. The
aim is to build a repository that is able to handle the different
complex forms of educational resources and a desktop application
that eases the processes needed to be taken by a user to share
his/her educational resources. The solution proposed is centered
on the front-end application which handles the complex objects on
a users desktop. The desktop application will handle all the
needed processes with minimal interaction with the user to ingest
learning objects into the repository.
|
|
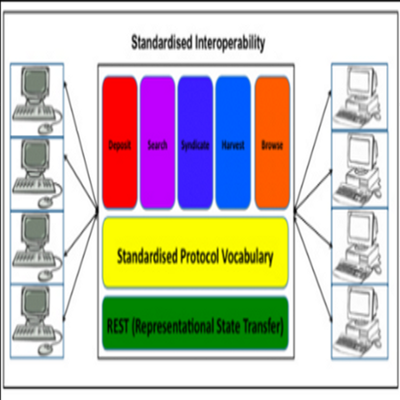
Meta-standardisation of
Interoperability Protocols
Interoperability is the capability of heterogeneous systems to
communicate and exchange data with each other, using a set of
pre-defined formats that will allow the systems to interpret the
data exchanged correctly and use each other's services
successfully. The current suite of high-level interoperability
protocols is made of either simplistic and easy to implement
protocols that lack some efficiency or efficient but hard to
implement protocols. The implementation of more that one protocol
requires the knowledge of different sets of vocabularies and
rules.
The ever-increasing number of online digital repositories
require an easy to implement but still efficient and
standardised protocol framework, that will act as an incentive
to interoperability and open access. The aim of this project
is to provide an experimental set of protocols developed on
top of a standardised framework.
|
|
Distributed texture-based terrain
synthesis
We generate realistic terrains by combining user-sketched curves
and real landscape data in a patch-based synthesis to produce
terrains with features that reflect user constraint curves and the
characteristics of a real terrain. This process involves the
manipulation of large landscape data which is extremely
time-consuming and so a GPU implementation is used to increase
performance.
|
|
Cloud Computing for Digital Libraries
With the ever-increasing volumes of research documents produced
over the years, in the form of electronic thesis and dissertations, the
existing information management systems cannot sacle well and hence
dynamic scalability of cloud computing can be taken advantage off to offer
this service. This research thus, aims to develop techniques for building
scalable digital information management systems based on efficient and
on-demand use of generic grid-based technologies. In particular, existing
resources like the Amazon Elastic Compute Cloud (Amazon EC2), Amazon
Simple Storage Service (Amazon S3) and Amazon SimpleDB were used in this
study.
|
|
Designing Digital Storytelling for
rural African Communities
| By |
Thomas Reitmaier |
|
Website |
None |
This research aims to situate digital storytelling within rural
African communities. We design and build a mobile digital
storytelling system on top of insights that arose out of
ethnography and a design workshop held in a rural village in the
Eastern Cape of South Africa. We use this system to further
situate digital storytelling by probing how rural African
communities interpret digital storytelling and how the practice
fits into the oral culture and social fabric of such
communities.
|

|
Using a Content Management System as
a Front End to a Digital Library System to Improve
Usability
Digital Library systems are still immature software, known to be
difficult to deploy and use. One of the difficulties in deployment
is customisation of the interface, and integration into an
existing website. Digital Library systems don't tend to use
templating systems to allow web designers to re-skin the system,
like popular Content Management Systems do. This project aims to
integrate a Digital Library system into a Content Management
System, to provide the advantage of templating and more easily
integrate with an existing Content Management System-driven site.
|
|
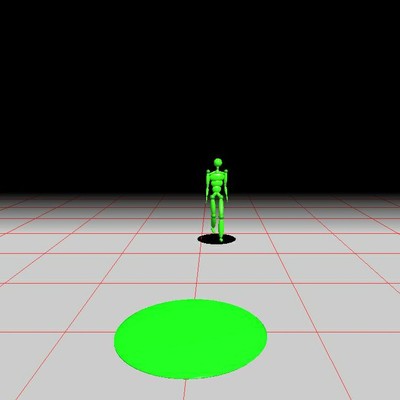
Skeletal Character Animation
| By |
Warren Russell |
|
Website |
None |
The focus of this research is on the rapid creation of motion
graphs for use in skeletal character animation. To speed up the
graph creation process, we have focussed on the comparrison of the
frames of animation that are being used in the graph. Instead of
comparing every frame of aniamtion to every other frame of
animation, we have divided the space that the skeleton occupies
into a regular 3D grid. By grouping the positions of the
skeleton's joints into buckets based on the cell they are in, we
have found speedups to the comparrison process of up to 125
times.
|
|
Draggable Tag Clouds: a means of
Abstract Query Specification for Information Retrieval
Draggable tag clouds are a proposed extension to the standard
tagging metaphor that exploits the spatial proximity between
tags. Tag clouds are static, visually weighted renditions of
clusters of terms that interface to the prevalent concepts of
collections of information. Draggable tag clouds may act as a
search user interface that affords the user the opportunity to
rearrange tags within the tag cloud space as a means to
approximately express their information need. The closer a tag
appears to the cloud’s centre, the greater its significance to the
user. To examine the utility of this proposed extension, the
draggable tag cloud search user interface was linked to Google
News, allowing users to search news content by continuously
modifying the tags’ positions.
|
saunder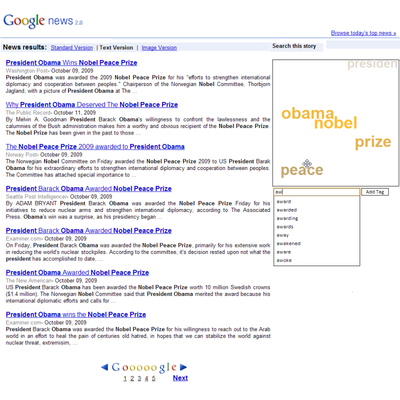
|
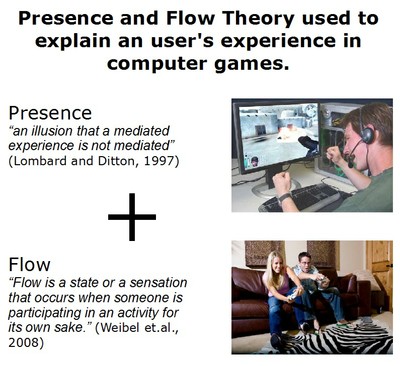
Flow and Presence in Games: Flow as a
companion theory to Presence theory to explain user experience
in Games
Currently Presence theory is used to explain the sense of presence
a user experiences in a virtual environment; this theory does not
take into account many psychological aspects. Flow theory however
does and is used to explain social psychological and behavioural
aspects. Two questionnaires were selected which would best
represent this compatibility in a game: Fallout 3 (by Bethesda
Game Studio); for Flow theory: the FSS-2 – General and for
Presence theory: the ITC-SOPI. The data from these questionnaires
would be analysed for any similarities and differences and
contribute to a more well-rounded explanation of an user's
experience(s) in a game.
|
|
Designing a mobile-based business
development service for NGOs working with
micro-entrepreneurs
ICT4Dproject aims to aid NGOs working with micro-entrepreneurs in
South Africa. In particular, I am working with an NGO called
Triple Trust Organisation in an attempt to improve their
effectiveness in working with spaza shop owners in Khayelitsha and
the surrounding area. Since computers are not common in these
areas, cell phones will be used as the technology platform. The
project will fit into the research area of small-screen form
design, with some emphasis on touch-screen devices." A
representative image: is attached. It is not a picture of mine,
because I seem to have misplaced the pictures I took.
|

|
Autonomous Aerial Coverage of Areas
in a 3-D Environment Using Auction Algorithms
In the field of task automation, multiple robots are often
coordinated to accomplish tasks more efficiently. In certain
situations, a distributed algorithm run onboard all robots is best
used for task allocation. The aim of this project is to construct
a simulation which uses a distributed auction algorithm to
allocate path plans to Unmanned Aerial Vehicles (UAVs) in order to
survey irregular areas of uneven terrain. Additionally, the
simulation should be robust against communication faults and
produce solutions which are physically feasible.
|
|
A modular game engine for teaching
video game programming
The video game industry is maturing. Video game production
required powerful and robust tools to ease development. Game
engines are specialised middleware that take care of much of the
technical details allowing the game creators to concentrate on
game creation. A game engine is a valuable tool in game
programming education, but they are made for performance and
utility, not education. A modular game engine would allow students
to quickly make games using built in functionality, but also
allows them to alter an extend the current engine.
|
|
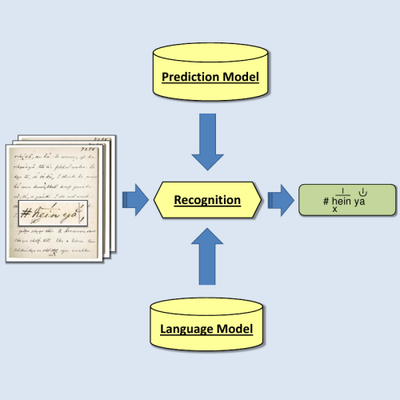
Learning to Read Bushman: Handwriting
Recognition for Bushman Languages
The notebooks in the Bleek and Lloyd collection contain
handwritten stories that metaphorically encode the Bushman
culture. These notebooks, however, only exist as scanned images
and therefore the stories they contain cannot be searched, indexed
or compared. This research seeks to investigate how accurately the
Bushman stories can be automatically converted from images to
text, through a process known as transcription, and also to
explore the various techniques for doing this with a strong focus
on the complex diacritics that are used in the Bushman script.
|
|
Alumni
2010
- Johannes Jansen van Vuuren
- Paolo Pileggi
- Gustavo Salazar
- Calvin Pedzai
- Lekometsa Mokhesi
- Anton Eicher
2009
- Shikoh Gitau
- David Jacka
- Alex Karpul
- Juan-Pierre Longmore
- Ashley Reid
- Christopher Parker
- Andrew Symington
- Grace Kamulegeya
2008
- Stephen Asherson
- Sarah Brown
- Ming Chong
- Kurt Kruger
- Peter McMahon
- Ndapandula Nakashole
- Marlon Paulse
- Samuel Ogunleye
- Chen Wei
2007
- Leonard Ah Kun
- Chris de Kadt
- Jonathan Jedeikin
- Ken Lee
- Rudy Neeser
- Mayumbo Nyirenda
- Muammar Omar
- Sam Perumal
- Michael Scheibe
- Christoffel Schoeman
- Nemanja Spasic
- Reinhardt van Rooyen
- Yaqueen Gasant
- James Mutuku
last modified
2013-05-20 15:31
|
































